Forensically Sound Extractions, Verifiable Disk Imaging
When accessing a locked system during an in-field investigation, speed is often the most important factor. However, maintaining digital chain of custody is crucial when producing court admissible evidence. Elcomsoft System Recovery contains features to help establish and maintain digital chain of custody throughout the investigation.
In order to preserve digital evidence, the chain of custody begins from the first point of data collection. Elcomsoft System Recovery employs a forensically sound workflow to ensure that digital evidence collected during the investigation remains court admissible. The workflow implements read-only, write-blocking access to the target computer, and saves collected evidence in the form of digitally signed, verifiable disk images, making Elcomsoft System Recovery a viable alternative to hardware-based write blocking disk imaging devices while offering real-time access to crucial evidence.
Write-blocking disk access
Elcomsoft System Recovery helps producing court admissible evidence with write-blocking mode and read-only disk imaging. The write-blocking mode is engaged by default during the first steps of running Elcomsoft System Recovery, ensuring that no data is modified on the target computer. Write-blocking disk access is the tool’s default behavior. Experts must explicitly untick the “read-only” box to access system management functionality such as resetting Windows user and administrative passwords.
Verifiable disk imaging
The disks can be imaged into verifiable .E01 images. Together with read-only access, the use of hashing helps establish digital chain of custody, while employing the industry-standard .E01 format makes the images compatible with third-party forensic tools for comprehensive analysis. Whether the disk is imaged into a RAW/DD or the newly supported .E01 format, Elcomsoft System Recovery calculates a hash file and places it alongside with the image. The hash values calculated during collection can be used to authenticate evidence at a later stage.
Improved Full-Disk Encryption Workflow
Elcomsoft System Recovery makes it easier to access data stored in encrypted disks and containers. With automatic detection of encrypted volumes, ESR will automatically extract hashes required to launch an attack[1] on the password of the encrypted volume, saving them to the flash drive to offer faster access to encrypted evidence compared to the traditional workflow. In addition, ESR can extract and save hibernation files that may contain the encryption keys to access information stored in encrypted volumes. These keys can be used to instantly mount encrypted volumes or decrypt their content for offline analysis[2].
Encrypted Virtual Machines
In the world of hi-tech crime, encrypted virtual machines become one the most widely used cover-up tools. Manually locating such virtual machines can be an involving and time-consuming process. We made your work easier by finding many types of encrypted virtual machines automatically. Better yet, ESR will automatically capture the encryption metadata you’ll need to launch the attack on the VM encryption password in Elcomsoft Distributed Password Recovery.
Reset or Recover Windows Account Passwords
Up to 40% of support calls are related to forgotten passwords and locked logins. Elcomsoft System Recovery helps instantly reset Windows system passwords, enabling system administrators regain access to locked Windows accounts. Supporting local Windows accounts, network domains and Microsoft Account, Elcomsoft System Recovery is a must-have tool for network administrators, IT professionals and security specialists.
Reset or Recover SYSKEY Passwords
SYSKEY passwords were a dubious and controversial way to add an extra layer of security to Windows login. Used in older versions of Windows, SYSKEY passwords were removed from Windows 10 and Windows Server 2016 release 1709. An unknown SYSKEY password blocks Windows startup and prevents the ability to recover or reset the user's account password.
Elcomsoft System Recovery can reset SYSKEY passwords in order to restore the system’s normal boot operation. Before resetting a SYSKEY password, ESR will now check whether this operation is safe for the system.
In addition, Elcomsoft System Recovery allows looking up for cached SYSKEY passwords in various system databases and cache files before resetting.
Instant Reset and Configurable Attacks
Elcomsoft System Recovery can reset account passwords instantly, while supporting pre-configured attacks to recover the original passwords. In addition, users can upload their own custom dictionaries for high-performance dictionary attacks with up to 4 levels of mutations.
Elcomsoft System Recovery unlocks locked and disabled user and administrative accounts in Windows 7, 8, 8.1, Windows 10, as well as many legacy versions of Windows including Windows Vista, Windows XP, Windows 2000, Windows NT as well as the corresponding Server versions up to and including Windows Server 2019. Both 32-bit and 64-bit systems are supported.
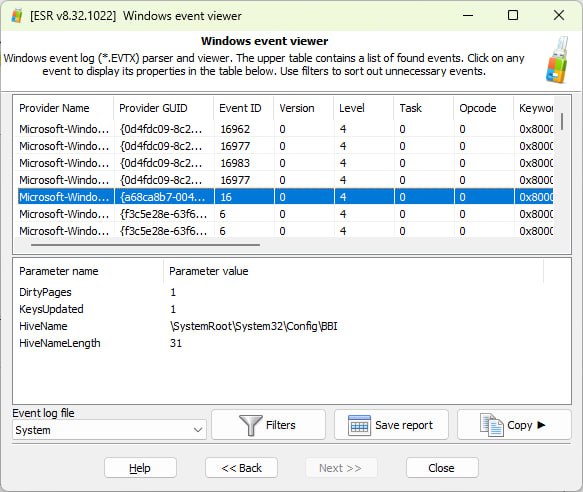
Built-in Viewer for Windows Event Logs
Elcomsoft System Recovery has an integrated log viewer enabling quick access to Windows event logs (EVTX files). For computer forensic and law enforcement specialists, analyzing Windows event logs is essential as these logs provide information about system activity, including login attempts, connected devices, and software installations. These logs can help trace unauthorized access, uncover malicious activities, and establish timelines, all of which are vital for investigations.
Ready to Boot, Immediate Assistance, Easy to Operate
Elcomsoft System Recovery comes with everything to quickly create a bootable DVD or USB flash drive. The image is based on a customized Windows PE environment, and comes pre-configured with a number of drivers to allow seamless experience on most legacy and cutting-edge hardware configurations.
Create a bootable USB drive or DVD disc in a few easy steps for immediate assistance. Elcomsoft System Recovery comes with 32-bit and 64-bit UEFI and legacy BIOS configurations, allowing you to create bootable media for all types of systems.
The genuine Windows PE environment offers complete access to the familiar Windows graphical user interface. No command line scripts and no poor imitations of the Windows GUI!
Case Studies
Elcomsoft System Recovery is an all-in-one security tool for Windows accounts. The tool helps detect and resolve a variety of issues related to user and administrative account passwords.
- Perform forensically sound data collection
- Do in-field analysis and disk imaging
- Collect court admissible evidence during in-field investigations
- Assign Administrator privileges to any user account
- Enable and unlock the locked and disabled user accounts
- Create forensic disk image for subsequent in-lab analysis
- Change and reset passwords for any local accounts
- List all local user accounts and highlight Administrator accounts
- Look up account privileges
- Detect accounts with empty passwords
- Instantly recover certain passwords to special/system accounts (e.g. IUSR_, HelpAssistant, etc)
- Backup and restore SAM/SYSTEM files
- Optionally restore original SAM/SYSTEM files after successful logon with a new password
Add more capabilities
Elcomsoft Encrypted Disk Hunter
Elcomsoft Encrypted Disk Hunter is a free, portable command-line tool to quickly discover the presence of encrypted volumes when performing live system analysis.
Multiple Windows, Linux and macOS full-disk encryption tools are supported including TrueCrypt/VeraCrypt, all versions of Microsoft BitLocker, PGP WDE, FileVault2, BestCrypt and LUKS. The tool must be launched with administrative privileges on the live system being analyzed. If an encrypted volume is detected, a further investigation of a live system might be needed to preserve evidence that could be lost if the computer were powered off.
» Read more about Elcomsoft Encrypted Disk Hunter in our blog
-
Elcomsoft Distributed Password Recovery is required to recover passwords to encrypted containers.
-
Elcomsoft Forensic Disk Decryptor is required to search for encryption keys, mount and/or decrypt encrypted volumes.